
The Growing Menace of Social Engineering Scams
Brought to you by Microsoft

Worldwide, social engineering scams continue to be a menace.
Confirmed fraud cases from BioCatch clients alone included a 24% increase in social engineering scams between 2020 and 2021. According to the U.S. Federal Trade Commission, impostor scams were the No. 1 type of fraud reported by consumers; in the UK, losses to authorized push payment scams topped card fraud for the first time in 2021, as reported by UK Finance.
Financial institutions have struggled with how to address the challenge of social engineering scams. The problem with these scams is that the criminal does not interact directly with the bank; instead, they convince the victim to execute the payment themselves. Device, IP address and location-based authentication controls will appear genuine. Even in cases where the bank detects risk and requires step-up authentication, such as two-factor authentication, a legitimate user performing the transaction will pass the challenge.
Fraud prevention solutions built on device elements and network data points are no match for criminals who have learned to spoof them. Banks need deeper visibility into risk, including behaviors associated with each step of the digital banking journey.
Every Swipe Tells a Story
Tech that uses behavioral biometrics can play a crucial role in helping financial institutions identify and stop social engineering scams. Even when a genuine user makes a payment, subtle changes in digital behavior can build a picture of the user during a digital session that suggests they’re inadvertently participating in a social engineering scam. Below is a summary of the emotions a victim of social engineering may exhibit during a scam, and how to interpret the associated behaviors.
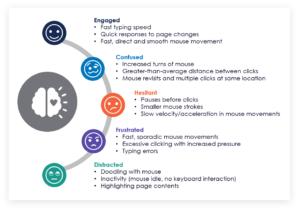
Each individual behavior on its own does not imply social engineering. But when combined with hundreds of other behavioral, device and network data points and compared against the norms of the genuine population, these insights could indicate that a scam is underway.
Consider something as simple as a customer who is on an active phone call while using the mobile banking app. Indicators for this activity are significantly different than what genuine behavior looks like, based on what historical data analysis tells us:
- Less than 1% of all Android users multitask, combining a phone call with mobile banking activity.
- More than 25% of confirmed cases of fraud show that the victim was on an active phone call.
- Data shows that an active call is 30 times more prevalent in the fraud population than the genuine population.
When considering these differences, an active call during a live banking session can be used with other data points to strongly indicate social engineering.
A Strategy to Address Social Engineering Scams
Regulators are paying more attention to this problem, especially given that victims don’t always get reimbursed following scams that involve “authorized” payments. In the U.S., legislators have expressed a growing interest in the problem as payment platforms, such as Zelle and Venmo, become increasingly popular targets for criminals. And in the UK, legislators are set to introduce rules that would require banks to reimburse victims of authorized push payment fraud. The time for financial institutions to shape the conversation is right now. Adopting a strategy to address the rise in social engineering scams should consider four key aspects:
Customer Protection Across All Account Types. Social engineering can be costly. All customers, regardless of their financial investment, are at risk. Our data shows that 53% of attempted payments resulting from social engineering scams were greater than $1,000.
Education to Inform Customers. Government regulation and industry initiatives are incentives for financial institutions to reimagine their consumer education programs. Besides avoiding financial losses and the impact on reputational risk, financial institutions can improve in consumer awareness as a way to brand differentiate.
Cross-Channel Protection. As with other fraud types, mobile applications are becoming increasingly popular with customers and criminals alike. In 2021, 88% of social engineering scams were carried out on a mobile device. With more customers using mobile banking applications to conduct transactions, social engineering scam detection should also be weighted to reflect this.
Incorporate Behavioral Biometrics. As social engineering scams overtake traditional account takeover fraud, implementing behavioral biometrics can provide visibility beyond device and network data points, improve your bank’s ability to identify high-risk transactions and significantly reduce fraud.
As social engineering scams rise worldwide and become increasingly challenging to detect, financial institutions must adopt new strategies to combat the threat of fraud and maintain customer trust.


